10 Ways to Improve your Business Cyber Security
Have you ever thought what would happen if your website got hacked? What about getting your sensitive company data leaked? Do you know if your business has strong cybersecurity mitigation plans to cope with the risks of remote working conditions?
Within a short period, the COVID-19 Pandemic has pressured many industries to perform a large-scale business operations shift. The pandemic situation escalated without warning, forcing many businesses to quickly transition to remote working.
Unfortunately, this means businesses with premature remote working policies are more vulnerable than ever to cyber threats. This suspicion is confirmed by Viljoen and Nunn-Price of Deloitte Australia (2020)1, who observed a sharp increase of around 400 thousand spam emails just in mid-March alone.
Despite this, the benefits clearly outweigh the risks. Many businesses, including ours, have already seen first-hand the increase in productivity after the transition to remote working . As the new normal seems to settle towards hybrid working (a combination of physical and remote working), now would be a good chance to review your company’s cybersecurity policies.
For more information about the benefits of remote working, read our blog on the topic here.
To make sure your business is well-equipped against cyber attacks, follow these 10 simple tips:
1. Ensure remote business meetings are secure from hijacks
Remote business meetings are necessary for successful remote working. However, there have been quite a few incidents where unwanted meeting participants gain access to meetings and bombard them with inappropriate materials (Novet, J. 2020)2. These hijacks, also known as Zoom-bombing, are very detrimental to your business image and relationship.
Here are some ways you can protect critical business meetings from hijacking threats when using some of the most popular online meeting applications:
Zoom
Google Meet
Google Meet doesn’t support passwords, but only attendees you invite through Google Calendar can join the meeting without approval. Other participants have to join the meeting through Meeting Codes, which then have to be approved manually by the host. Make sure you review who these participants are before you approve them.

2. Maintain files in the cloud with strong user access policies
Remote working conditions need the use of cloud storage for data. Make sure you maintain all business files within your company’s chosen cloud storage environment. Having your files in separate cloud platforms makes it harder to manage as well as increasing data redundancy.
You might also want to look into file access permissions. For example, you can restrict your company’s Financial Report folder to be viewable by the management team but editable only by your Accounting department, for example. Each cloud platform has different ways to do this. Here’s how you can do it in Google Drive and Dropbox.
3. Backup your files and website data regularly
Backing up your data in multiple locations is a good idea in case of data loss incidents. Generally the more backup locations you store your files in, the better.
Below are some options of backup media you can try:
4. Change your passwords regularly
Think about this – what if there’s someone out there that attempts to log in to your user accounts every minute? What if they try out every single combination of characters to work out what your correct password is? This type of attack, better known as brute-force attack, happens more often than we think and it could very well be happening to your user accounts right now.
We’ve recently looked at our website login attempt logs and found out that brute-force attacks were being done on our website every minute, and we had to act quickly to improve our security!
These attacks are usually done with the help of computer bots. The bots will try to guess random password combinations and remember them if they fail. This process will be repeated until the user account is eventually breached. Usually the attacker runs multiple instances of these bots simultaneously to shorten the amount of time they take to guess the correct password.
Here are some tips to help you better protect your user accounts from brute-force attack attempts:
The more random the combination of alphabetic letters, numbers and symbols are, the more secure the password is from brute-force attacks. When creating passwords, we would recommend using a random password generator while also following the criteria above.

But how would you remember what the password is? If only there was a way to save the passwords in your computer somehow.
5. Don’t save passwords in your browser – use Password Manager platforms instead
With the introduction of password saving features in web browsers, gone are the days where someone has to write down their passwords in a notebook. But is it truly safe to trust your browser with your passwords?
At its first inception in 2008, Chrome used to store all saved passwords in your computer without additional encryption (The Guardian 2008)3. Anyone could simply open up the browser’s settings page and view the passwords in plain text.
This has been rectified and now Chrome, just like other major web browsers, requires you to fill out a password (called Master Password) before you can view the saved passwords in plain text form. No harm done, right?
Unfortunately, there’s still another problem with saving passwords in web browsers – the autofill feature. Once the password is saved to a website, the web browser will automatically fill out the username and the password for you every time you get prompted to login. Your web browser won’t verify your identity when you enable this feature. This means anyone can login to your user accounts, provided they have access to your device and the web browser you’re using. Simply put, using the browser’s built-in password autofill feature trades your security for convenience.
Once the password has already been autofilled, anyone can even change the password field to display in plain text format through some minimal web editing.
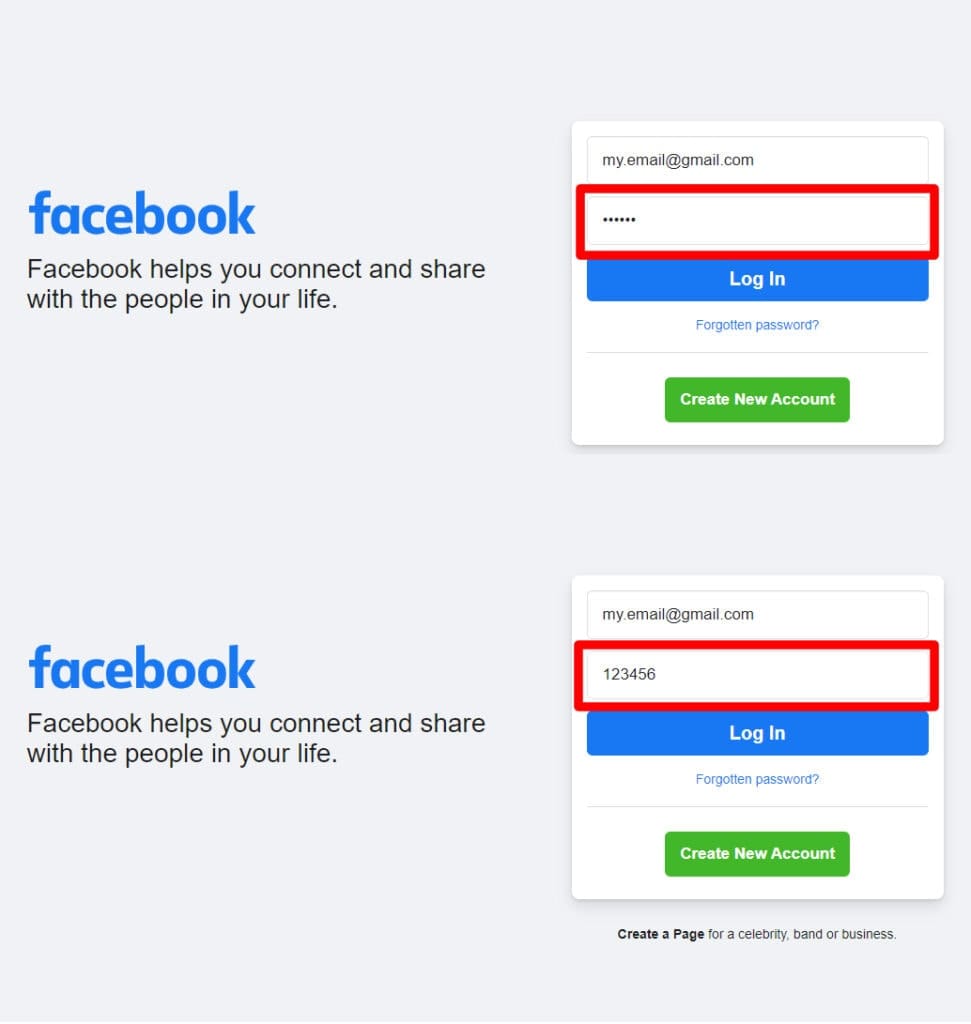
All done in a minute. Scary to think anyone can find out what your password is, isn’t it?
Our recommendation in this case is to use password managers instead. You gain the convenience of the password autofill features while maintaining your security. You can easily fill out passwords with the click of a button. But to do this, you are required to enter a password (i.e. Master password) when accessing the password managers.
There are several reasons why these platforms are better than a web browser’s save password feature:
Some of the most well-known password managers we would recommend are LastPass and PassCamp.
6. Use Two-Factor Authentication (2FA) if possible
A Two-Factor Authentication (2FA), also known as Multi-Factor Authentication, is a term for additional security measures used in conjunction with a user’s password for verification. These act as extra passwords you need to enter within a limited amount of time. Once it expires, the code will then be randomised.
Whenever you can, 2FA should always be enabled. In case your password has already been cracked, the attacker will still need to figure out the correct 2FA code in a short time frame before they can breach your account.
Most 2FAs are set up by scanning a QR code on your mobile device within an authenticator app like Authy or Google Authenticator. Once your device is linked, you will be given recovery codes that you can use to login if you ever lose your device. Make sure you save these, but don’t store them in your computer – either write these down or store them in your password manager for safekeeping. It should be done this way to prevent the attacker from easily learning what your recovery codes are if they ever gained access to your computer files.
7. Provide employees with sufficient training and documentation
Every year an analysis of the cyber landscape confirms one thing: human errors remain one of the major reasons for successful cybersecurity breaches. Confirmed by 2019’s analysis from the UK-based cyber security firm CybSafe (2020)4, 90% of 2376 cyber breaches in the UK are attributed to human error.
Ahola (2019)5 states that most of these errors are simply caused by a lack of awareness by illustrating how phishing attempts work more effectively against people who are less wary of them. He also suggests that companies should start tackling this issue to make their business more secure.
We recommend documenting all your business practices, processes, and procedures within a centralised management system. This not only mitigates the human error issue, but also gives you a head start in meeting the requirements of the ISO 9001:2015 Quality Management Systems Standard.
8. Be wary of phishing links and spam emails from fake email accounts
Modern spam emails have come a long way from looking dubious. These days there are all sorts of clever tricks to make spam emails and phishing links look legitimate at first glance, whether by imitating a website or a real person. We’ve had a couple of incidents where these seemingly come from someone from our team, until we found out they came from an unknown email address.
Below are some questions you can ask to find out if an email is a spam:
Be extremely careful of links within suspicious emails. Some malicious links (phishing links) can inject malware or even steal your data. If you think you ever clicked on one, make sure you follow these steps:
For more information about scam emails and phishing scams, please visit https://www.cyber.gov.au/acsc/view-all-content/threats/phishing.
9. Review software being used across the business
Do you know if the software you’re using is being updated regularly?
Are your employees using different software platforms for the same purpose?
The more platforms you use, the harder it is to maintain and the easier it is for cyber attacks to slip through. Outdated software tends to also be the weakest chain in your cybersecurity protection, especially if they have known vulnerabilities that weren’t patched at that point of time.
We suggest maintaining a regular schedule for updating software and keeping a list of all software platforms being used up to date. An easy way to keep this manageable is by using your password manager to keep track of all software being used within your business.
10. Deny access from ex-employees
Make sure you always take the following measures for safety whenever employees leave:
If the pandemic has taught us anything, all businesses moving forward have to be ready to adapt with the changes, especially in their cybersecurity plans. With the move to remote working, all businesses nowadays not only have to be scalable but also be more primed to face cyber threats.
We hope this got you thinking about how you can develop strong cybersecurity plans for your business.
References:
1Viljoen, T. & Nunn-Price, J. 2020, “Actions to managing Cyber Security during COVID-19”,
https://www2.deloitte.com/au/en/blog/financial-advisory-financial-services-blog/2020/managing-cyber-in-the-remote-workforce.html.
2Novet, J. 2020, “Intruders are hijacking Zoom calls with noise and gross images — here’s how to avoid becoming a victim of ‘zoombombing’”,
https://www.cnbc.com/2020/04/02/how-to-avoid-becoming-a-victim-of-a-zoombombing-on-zoom-video-calls.html.
3The Guardian 2013, “Google Chrome security flaw offers unrestricted password access”,
https://www.theguardian.com/technology/2013/aug/07/google-chrome-password-security-flaw.
4CybSafe 2020, “Human error to blame for 9 in 10 UK cyber data breaches in 2019”,
https://www.cybsafe.com/press-releases/human-error-to-blame-for-9-in-10-uk-cyber-data-breaches-in-2019/.
5Ahola, M. 2019, “The Role of Human Error in Successful Cyber Security Breaches”,
https://blog.usecure.io/the-role-of-human-error-in-successful-cyber-security-breaches.
About the author
Richard is in charge of the IT operations and develops, implements, and manages the ISO Certification Experts website. Richard has a strong passion for UX design.
All information on this blog site is for informational purposes only. As this information is based on our professional experience, opinion, and knowledge, we make no representations as to the suitability of this information for your individual business circumstances. Especiality Pty Ltd trading as ISO Certification Experts and all related businesses and brands will not be liable for any errors, omissions, legal disputes or any damage arising from its display or use. All information is provided as is, with no warranties and confers no rights.
We will not be responsible for any material that is found at the end of links that we may post on this blog site. The advice, ideas, and strategies should never be used without first assessing your own personal business situation or seeking professional and/or legal advice. Information may also change from time to time to suit industry and business needs, requirements and trends.












